What is Code Injection?
Code Injection is an attack injecting malicious code that will be interpreted/executed by the application. In most cases, hackers inject SQL code to perform illegal operations in your database.
Why would SQL Injections target PowerBuilder Applications?
By nature, PowerBuilder applications are database-intensive and mission critical.
They handle large volumes of important data, which make them premium targets for hackers.
SQL injections attacks may :
- Access/destroy sensitive data (company info, client personal or financial data…).
- Get a description of the DB structure, table names…
- Take control of your DB Server, result in denial of access, hostile takeover...
How to Prevent SQL Code Injection attacks?
A typical strategy for SQL injection (SQLI) consists in entering a malicious SQL statement in a form field, instead of the information you were expecting.
In PowerBuilder applications, Dynamic SQLs (i.e. SQL statements embedded in PowerScript events and functions) are particularly vulnerable and should be reviewed carefully.
Non compliant code code should be replaced with an equivalent - and compliant - set of instructions.
Example of non-compliant code:
string query = "DELETE FROM employee WHERE emp_id = '" + Emp_id_var + "'" ; EXECUTE IMMEDIATE: query;
Example of compliant code:
INT Emp_id_var = 56 PREPARE SQLSA FROM "DELETE FROM employee WHERE emp_id =? " ; EXECUTE SQLSA USING :Emp_id_var;
Visual Expert can automatically perform this verification to identify such security vulnerabilities.
How to Protect PowerBuilder Apps against Code Injection Attacks?
Your first option is to list all Code Injection vulnerabilities found. (See Below)
Later in this article, we will see how to inspect a particular object, library or package.
Listing all Code Injection vulnerabilities found in your code :
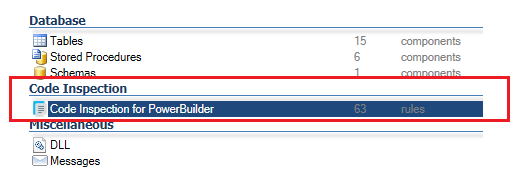
- In the Main View, click on ‘Code Inspection for PowerBuilder’.
- In the Navigation Bar, click on 'Security Vulnerabilities'.
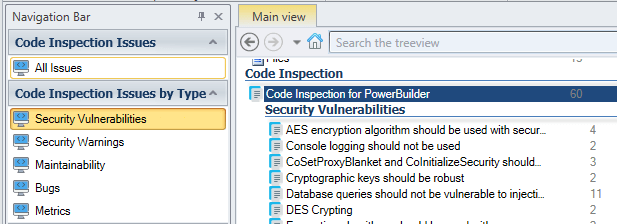
- Select the rule “Database queries should not be vulnerable to injection attacks”.
- Select ‘Issues Found’ in the Navigation Bar.
Visual Expert lists all the events and functions with SQL queries vulnerable to Code Injection.
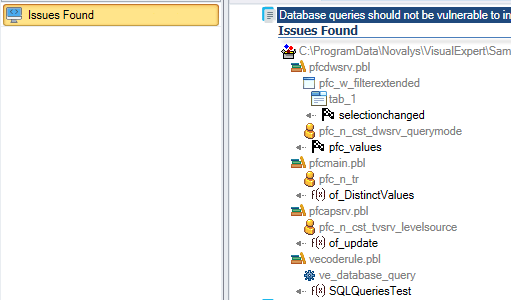
- Select a method from that list.
The instructions generating this vulnerability are highlighted in the code.
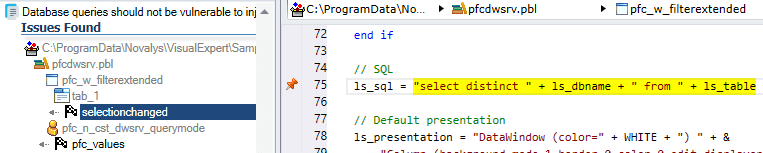
- To fix a 'Code Injection' issue, select the PowerBuilder function in the treeview.
- In the Navigation Bar, click on “Open in PB IDE”.
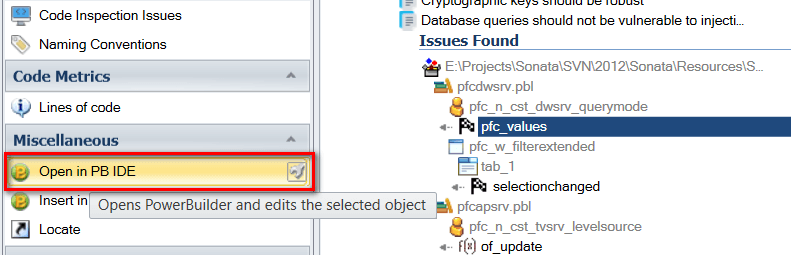
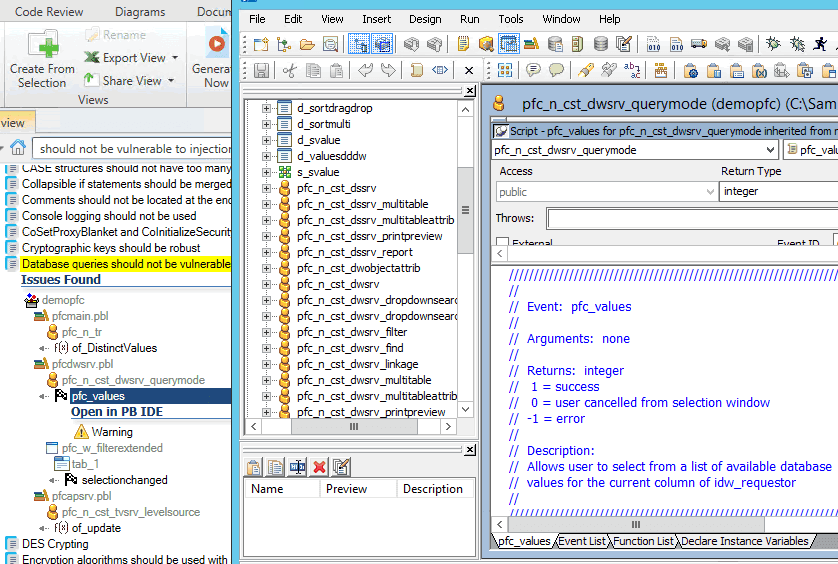
Visual Expert will open the corresponding target, object and Powerscript in the PowerBuilder IDE, under the condition that PB was previously opened with the proper Workspace.
You can then perform modifications and build/save your PB project.
After the next code analysis, Visual Expert will update 'Code Inspection' results according to your modifications.
Inspect a particular Object, Library, Package or Method
In case you wish to focus on a particular piece of code, you can follow these steps:
- In the Visual Expert Treeview, select the piece of code you wish to inspect.
For example a procedure.
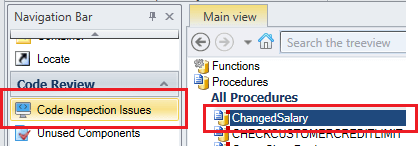
- In the navigation bar, click on “Code Inspection Issues”.
- Follow the steps 4 to 7 explained above.