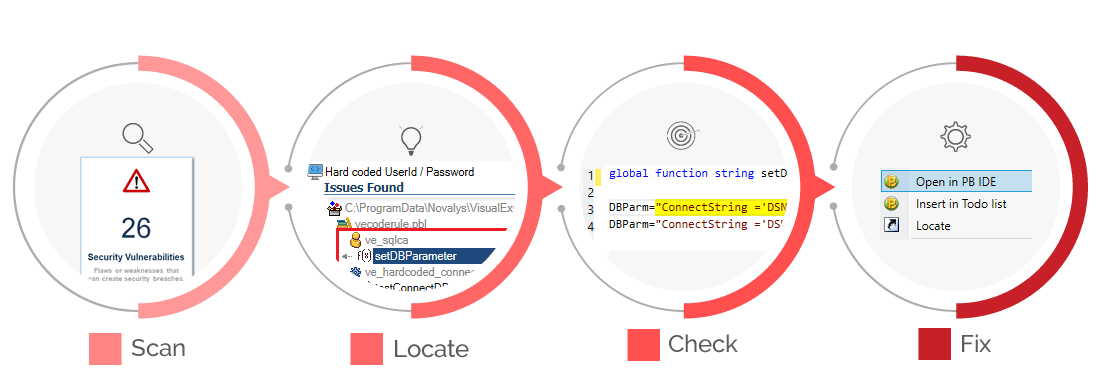
Detect Security Vulnerabilities in your Source Code
Visual Expert checks you code against predefined rules, detect vulnerabilities and locate them precisely.
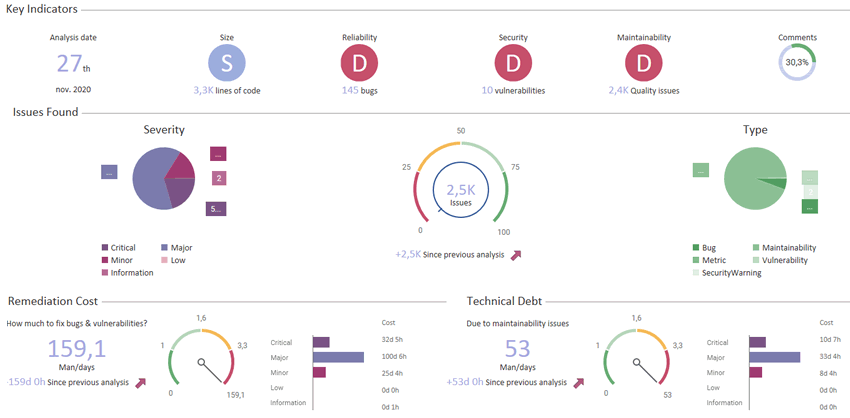
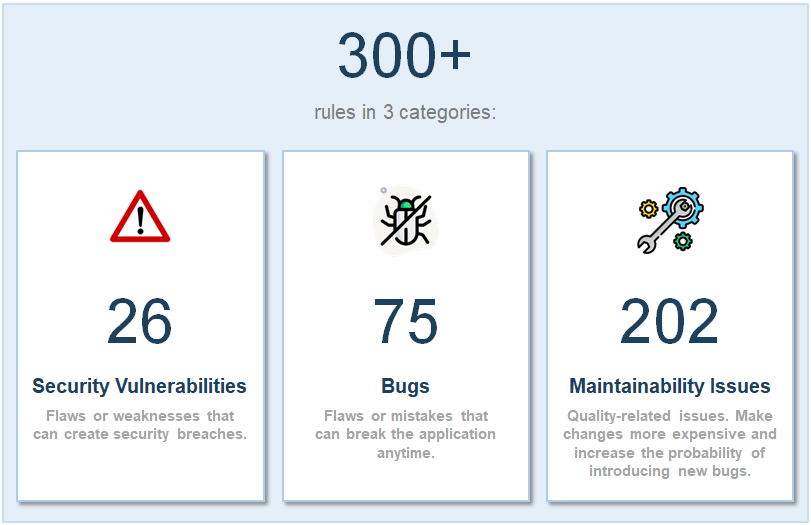
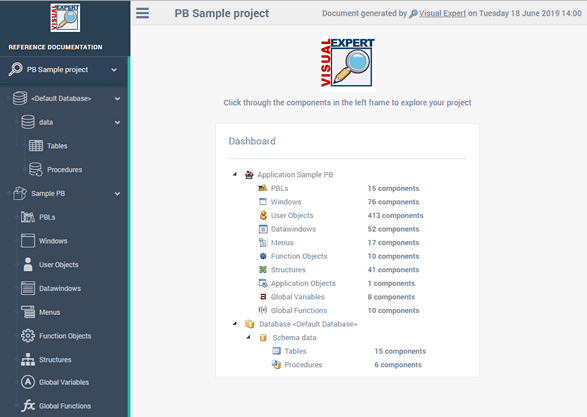
Code Inspection Dashboard
Easily find and fix issues in your code.
300+ rules to improve Security, Quality, and Maintainability.
Check your code under
various angles
- Detect and remove security vulnerabilities
- Comply with coding "grammar" standards
- Comply with code readability standards
- Architectural layering adherence
- Remove code duplicates
- Improve performance
- And more...
Preview the workload in a dashboard
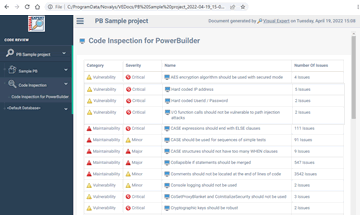
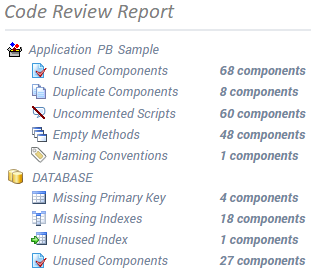
Generate Code Review Reports
Integrate Static Application Security Testing in your CI/CD Pipeline
Integrate with Jenkins or GitLAB.
Add a code inspection job in your Continuous Integration Workflow.
Perform a full code review each time a build is generated.
Reduce the time between building and fixing issues.
What are the security rules checked by Visual Expert?
- Always use AES encryption algorithm in a secure mode
AES offers several modes (ECB, CBC, CFB…), some of them being faster or safer. Your calls should leverage the most secure one. - Never use Console logging in production
Console logging is a method to find out what the code is doing. It should be disabled in production, as it could expose sensitive data. - Never use CoSetProxyBlanket or CoInitializeSecurity
Calls to subroutines CoSetProxyBlanket, CoInitializeSecurity and CoInitializeSecurityAlias can generate security breaches. - Encryption keys should be long enough
To make cryptographic keys robust against brute force attacks, they must have a sufficient key size. - Database queries should not be vulnerable to injection attacks
Code injection attacks can perform CRUD operations on sensitive database information through vulnerable queries. Identify SQL queries in your PB Code that accept data from the user because they are prone to injection.
- DES Crypting
The Data Encryption Standard (DES) is a symmetric-key algorithm for the encryption of digital data. Its short length makes it too insecure for digital data and should not be used anymore.
- Encryption algorithms should be used with secure mode and padding scheme
To secure your code using encryption algorithms, operation modes and padding schemes must be used correctly.
- Generic exceptions should not be ignored
CATCH blocks should always have a proper catching mechanism with a meaningful exception handling. - Hard coded IP address
IP addresses are sensitive information that should never be exposed in production. - Hard coded User Id / Password
You should never hard code user credentials on the production to avoid security attacks and data leak. - I/O function calls should not be vulnerable to path injection attacks
I/O functions accepting data from users, they are prone to Injection attacks (URL parameters, POST data payloads, cookies). Building file system paths from such data may resolve to a path that should not be accessible to users. - OS commands should not be vulnerable to injection attacks
If the execution of operating system commands is allowed from user data, it can lead to command line injections, creating a serious threat to the underlying operating system. - Regular expressions should not be vulnerable to Denial-of-Service attacks
Building a regular expression pattern from a user data is highly unrecommended and leads to security threats. - SHA-1 and Message-Digest hash algorithms should not be used in secure contexts
The SHA-1 and Message-Digest algorithms should not be used anymore because they are too simple to crack by the attackers.
Why Perform Security Scan with Visual Expert
High-quality analysis
In-depth analysis of your PowerBuilder code based on 20+ years of experience.
Early Correction
Discover vulnerabilities at an early stage to reduce the risks and the remediation costs.
Rapid Remediation
Immediately identify the code to be changed thanks to Visual Expert tools.
Continous Integration
Visual Expert integrates with Jenkins to enable continuous integration.
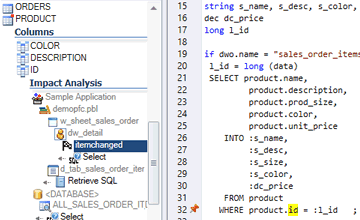
Impact Analysis
Assess the impact of a change in your code
Estimate what you should modify to accomplish a change.
Don't break your application after a change!
- If I change this variable, what is the effect on my code?
- If I add a parameter to a function, what else is affected?
- If a table or column is changed, which code should I update?
Scan for Security Vulnerabilities
Identify and fix Security issues in your code:
- Hard coded user id & passwords
- Hard coded IP addresses.
- Vulnerabilities to Injections attacks
- Fields access/protection issues
- Improper/unsecured use of encryption
- and more...
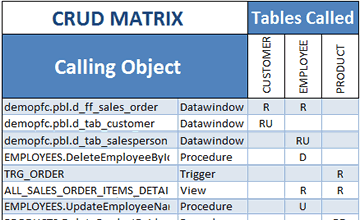
Review CRUD Operations in Your code
(Create, Read, Update, Delete)
Generate a CRUD matrix showing which programs access your data.
For instance, which DW or Procedures Create/Read/Update/Delete which Tables.
- Review dependencies between database and PB applications.
- Analyze the impact of changing your database Schema, for example changing a table definition or adding an index.
- Estimate software complexity and development efforts.
- Find out which table is never updated, deleted from multiple places, etc.
- Make sure every process has at least one input (R) and one output (CUD).
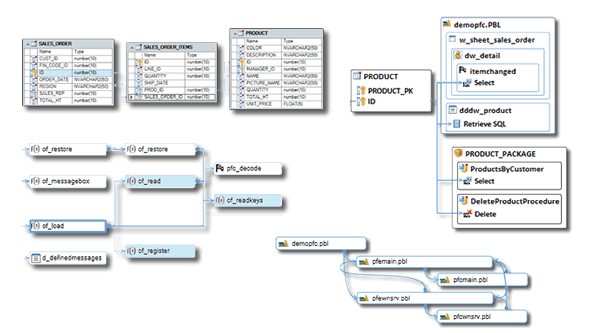
Generate Diagrams from your Code
- Visualize objects and dependencies.
- Diagrams and source code are synchronized.
- Select objects to generate a diagram
Visual Expert generates:
- Data Model Diagram to document graphically database entities and their relationships.
- Impact Analysis Diagrams to find all references to a table, column, object, method, variable...
- Call graphs to visualize chains of calls (multiple levels of references).
- PBL dependency diagrams to visualize dependencies between PBLs
Document your Code
Create reference manuals in HTML
Update your documentation on a regular basis (scheduled job).
Document the references in your code and navigate between these using hyperlinks.
Share knowledge with teammates.
Improve Code Quality
Cleanup the code. Streamline maintenance efforts. Avoid unexpected behavior.
- Identify unused objects and remove some dead code.
- Find empty methods, duplicated objects, oversized or uncommented scripts.
- Calculate code metrics: lines of code, number of objects, methods, variables…
- Check naming conventions.
- Find objects that do not inherit from an ancestor etc.
- You can check your code against hundreds of rules
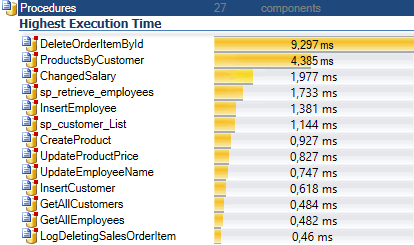
Improve Code Performance
Find slow pieces of code. Remove Bottlenecks
- Find the slowest procedures, functions, triggers
- Reduce the time to access a given table
- Break down the execution time of a large object into sub-queries or instructions.
- Decompose the performance of a chain of calls
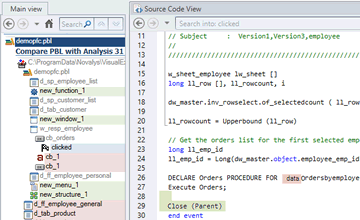
Code Comparison
Compare 2 versions of your DB or application:
- View differences in a container hierarchy.
- Drill down to find relevant changes.
- Filter changes for a given object, or object type: Userobject, Table, Procedure...
- Filter changes in a given PBL.
- Save “snapshots” of your code on a regular basis, and compare them anytime.
- And more...
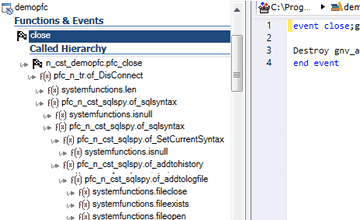
Understand Complex Code
Explore the application structure. Understand its inner working.
When maintaining complex Applications, you may need to learn more about the code.
In such cases, Visual Expert is the perfect companion for PowerBuilder.
Navigate in your code via hyperlinks: each reference comes with a link to the referenced item.
Tooltips provide useful information about objects, methods and variables.
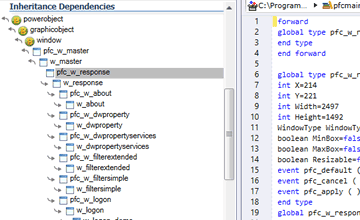
Explore inheritance dependencies between PB objects.
Lots of advanced feature will screen your code under various angles.
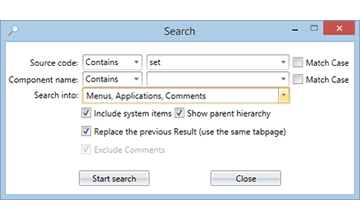
Advanced String Search
Visual Expert Global Search addresses common shortcomings:
String searches often return lots of results. They are usually tedious and unproductive.
- Use multiple criteria to reduce the search result.
- Restrict search to one or several object types.
- Search for exact words, or words starting/ending with, matching regular expressions…
- Search into several PB targets at the same time.
- Review results in a container hierarchy.
- The strings found are highlighted in the code.
- Filter relevant result items.
- Share the outcome with colleagues.
Catch a glimpse of Visual Expert
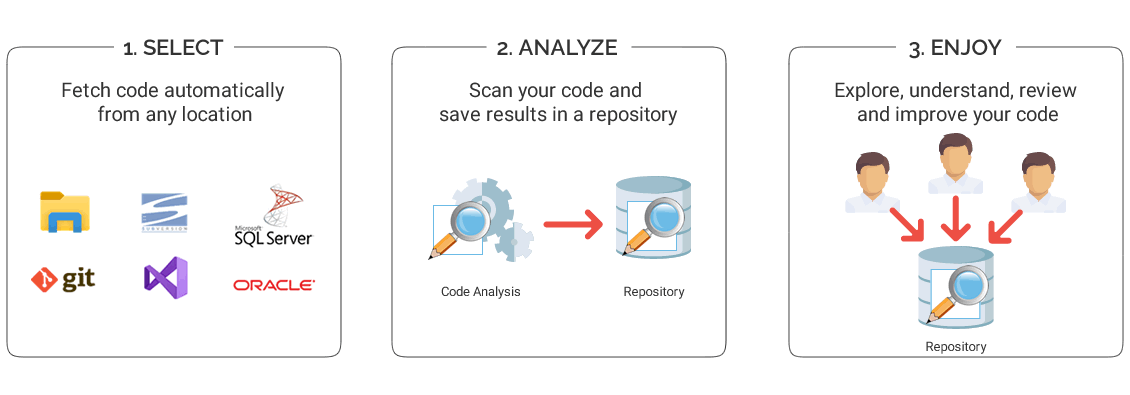
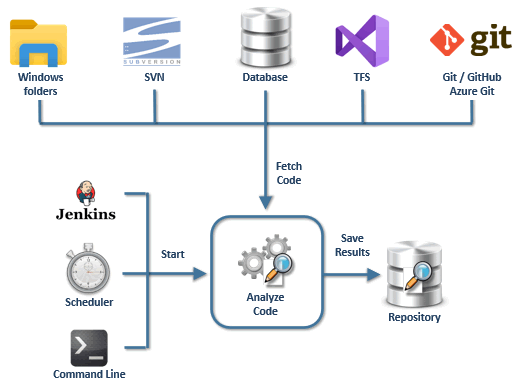
How it works?
Visual Expert Pricing & Editions
-
-
Basic
up to 500 000 Lines of Code$595 /user
/year- up to 500 000 Lines of Code
- Cross-References / Impact Analysis
- Code Inspection
- Performance Tuning
- Code Documentation
- Installation on a Client PC
- Updates
-
Basic
up to 500 000 Lines of Code$1,395/user
- up to 500 000 Lines of Code
- Cross-References / Impact Analysis
- Code Inspection
- Performance Tuning
- Code Documentation
- Installation on a Client PC
- Mandatory for the 1st year
- Updates - $279
-
-
-
Professional
up to 5 Million Lines of Code$1,195 /user
/year- All Basic Features, plus:
- Up to 5 million Lines of Code
- Analysis History
- Code Comparison
- Analysis Scheduler
- Collaborative Features
- Integration with DevOps Platforms
- Installation on a Client PC or a Server
- Updates
- Mandatory for the 1st year
- Premium Support - $1795
-
Professional
up to 5 Million Lines of Code$2,850 /user
- All Basic Features, plus:
- Up to 5 million Lines of Code
- Analysis History
- Code Comparison
- Analysis Scheduler
- Collaborative Features
- Integration with DevOps Platforms
- Installation on a Client PC or a Server
- Mandatory for the 1st year
- Updates - $570
- Premium Support - $1795
-
-
-
Enterprise
more than 5 Million Lines of Code- All Professional Features, plus:
- More than 5 million Lines of Code
- Volume Discount
- Updates
- Premium Support
-
Enterprise
more than 5 Million Lines of Code- All Professional Features, plus:
- More than 5 million Lines of Code
- Volume Discount
- Updates
- Premium Support
-
Feedback from our clients